Security Guidelines
This guide answers common security questions about the Business Suite and provides best practices for safe usage. Plugin-specific notes are included at the end.
JavaScript-Enhanced Plugins
Our plugins leverage JavaScript to offer unmatched customization, a top-requested feature that supercharges Grafana’s capabilities. With great power comes great responsibility—here’s how to use it safely.
JavaScript code can be edited in Edit mode by Admin and Editor users, potentially introducing vulnerabilities if not managed properly.
Grafana runs JavaScript in a sandboxed environment, minimizing risks. To further secure your JavaScript-enriched plugins, we recommend:
- Provisioning: Lock dashboards to prevent unauthorized changes.
- Access Restrictions: Limit who can edit panels.
Provisioning
Provisioning ensures end users can’t save dashboard modifications. Learn the ins and outs of this approach in our detailed video tutorial:
For more, check out our companion blog post:
Provisioning is ideal for production environments where stability is key.
Access Restrictions
Restrict Admin and Editor roles to trusted users only. Viewers can’t access Edit mode, eliminating accidental or malicious changes.
Plugin-Specific Recommendations
The following tips address security considerations for specific Business Suite plugins.
Business Text
You can set the default setting disable_sanitize_html = false to keep security restrictions in place. However, with that many action tags will be disabled. For instance, your panels will not display HTML elements like buttons.
disable_sanitize_html = true
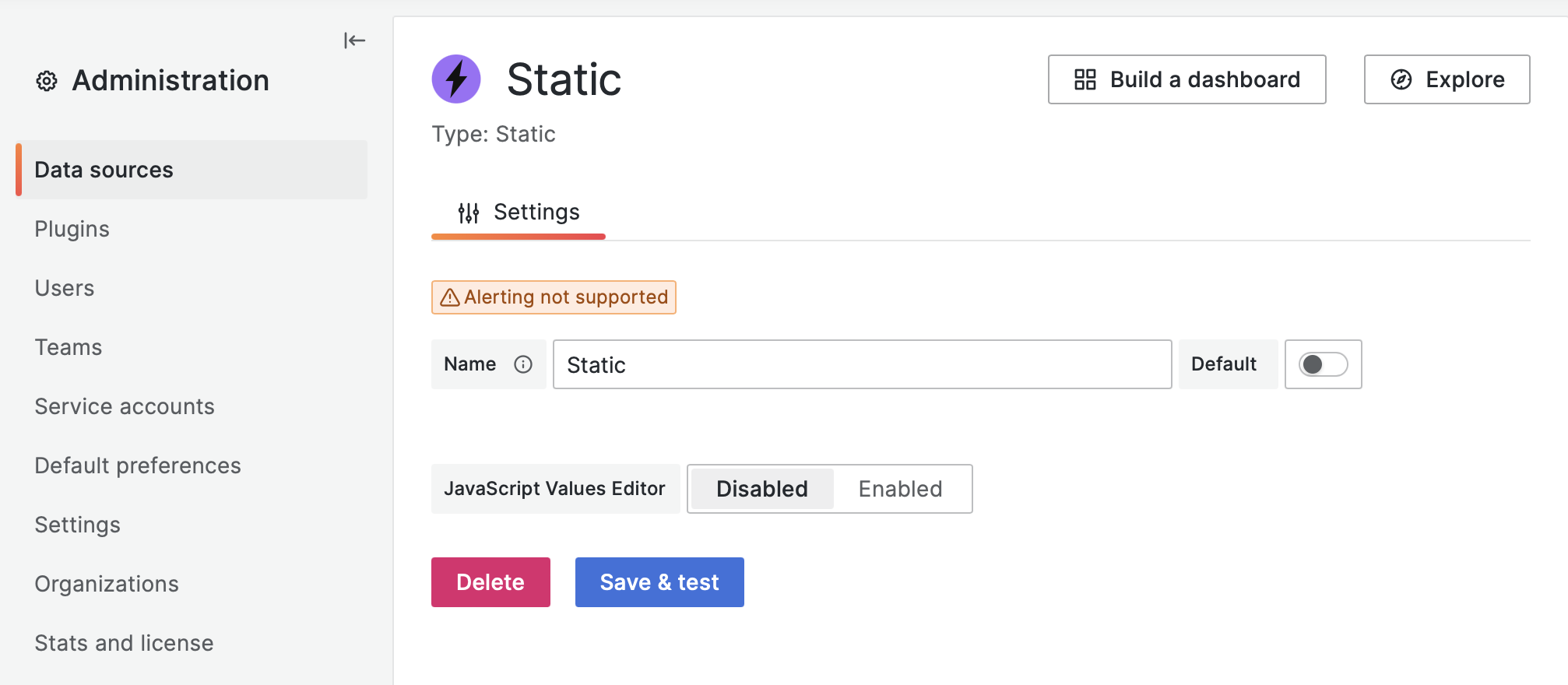
Business Input
The Business Input data source includes a JavaScript Value Editor, which can be disabled in the data source options for added safety:
Questions?
Have security concerns or need clarification? Reach out via GitHub or our YouTube channel!
Business Suite Enterprise partners please open Zendesk ticket for fast response.